Google’s recent move to introduce the “.zip” top-level domain (TLD) is raising eyebrows and alarm bells in the cyber security community.
We’re all familiar with top-level domains (TLDs) like “.com”, “.net”, and even the quirky “.pizza”. But Google’s newly released “.zip” has a dual identity – it’s not just a TLD, it’s also a well-known file extension used for compressed files.
And that’s where the trouble begins.
The Dark Side of “.zip”
On the surface, Google’s addition to the TLD pool seems like a minor, if quirky, update.
One of the immediate applications that springs to mind is as a link shortener, which has already been done. However, the situation isn’t quite as innocuous as it may first appear.
Thanks to their shared identity with a popular file extension, “.zip” domains can be cunningly employed by cybercriminals to trick users into clicking on malicious links.
It works like this:
- A cybercriminal registers a “.zip” domain with a common filename, such as “familyphotos.zip”.
- A user receives an email containing a link to “familyphotos.zip”, and they click it expecting to download a file.
- They’re instead sent to the malicious website.
- The website could serve a phishing page, or automatically download malware.
- Because the link appeared to be a zip file, the user will have increased trust and is more likely to fall victim attack.
The Dangers of Confusing Domain Names and Filenames
In essence, Google’s introduction of the “.zip” TLD has inadvertently weaponised a vast number of innocent file names overnight.
It’s the digital equivalent of turning everyday household items into tools of deception.
And as expected, bad actors are already exploiting this confusion to their advantage, registering thousands of “.zip” domains, such as “backup.zip”, “archive.zip”, “homework.zip”, and more.
White Hat Hackers to the Rescue
Some cybersecurity ‘white hats’ have registered a number of these domains to prevent them from falling into the wrong hands, essentially taking them off the market.
Others have repurposed the domains as protest platforms against Google’s decision.
However this won’t be enough to protect users from this threat.
A Legacy Feature Turned into a Modern Threat
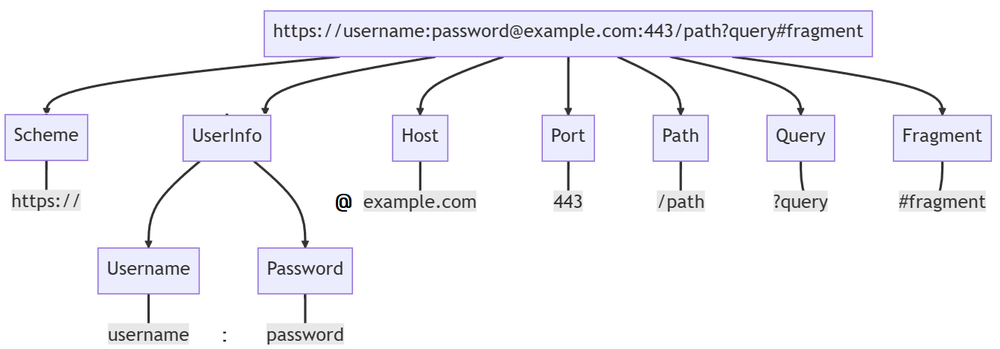
Another insidious application of the “.zip” domains involves a little-known feature of URLs called ‘UserInfo’.
This parameter can be used to specify login credentials for a web application, with the user being automatically authenticated when they’re sent to whatever domain comes after the “@”.
Although this feature has largely fallen out of favor due to the security implications of including plaintext credentials in a URL, it’s being exploited by bad actors in combination with the new “.zip” TLDs to craft convincing phishing links.
The Verdict: A Risk Worth Taking?
Google has come out in defense of their decision, stating that the risk of confusion between domain names and file names isn’t a new one. They cite the “.com” TLD as an example, which also used to be a common file extension. Critics, however, argue that this comparison is flawed, given the vast difference in the scale and prevalence of internet use and cybercrime between the early days of the web and now.
It’s worth noting that Google’s “.zip” is not the only new TLD causing a stir. The “.mov” TLD has also been called into question due to its shared identity with a popular video file format. Much like its “.zip” counterpart, the “.mov” TLD could be used by cybercriminals to create misleading links to malicious sites.
The jury is still out on whether the existence of the “.zip” TLD is a liability or simply a new variable in an ever-changing landscape. One thing is certain though: as long as the “.zip” TLD exists, users, developers, and security professionals alike will need to navigate its potential for misuse and deception.
What are your thoughts on the “.zip” TLD?
Do you think it’s a bad idea or is the Internet mature enough to handle it?