Back in 2014 CloudFlare, a CDN provider, announced free universal SSL for all their users. Which sounds pretty awesome, especially when you can sign up and use it on their free package. Free HTTPS traffic when search engines are begining to use it as a SEO rank? Yes please!
But what seems to be overlooked by many is that fact that the ‘Flexible SSL’ option only provides secure traffic between the user and CloudFlares network – NOT between CloudFlare and your website. Which means the users traffic is exposed over the internet as normal HTTP traffic.
In part I think CloudFlare is responsible for the confusion – they’ve focused on the marketing hype and neglected the security element.
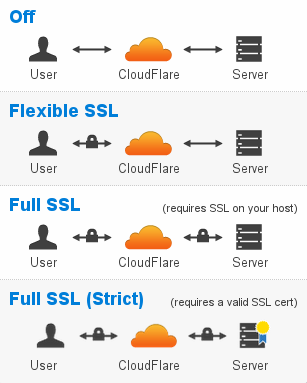
What they do provide is this diagram and descriptions for each level of SSL on offer.
Critically, people need to take note of the warning about flexible SSL:
NOTE: Flexible SSL is not recommended if you have any sensitive information on your website. This option should only be used as a last resort if you are not able to setup SSL on your own web server. This option is far less secure than the Full SSL option indicated below.
So what’s the problem with this? Well the website administrator may see this warning, they may accept this and choose to use the flexible SSL – that’s them choosing to accept the risk – but what about the website users?
Well the website users won’t know the difference! They’ll see HTTPS, see it’s a valid certificate and happily use the website, provide personal information, bank details etc – all without knowing that the underlying infrastructure results in their information going over insecure HTTP.
So when it comes to CloudFlare and SSL I advise you to steer cleer from the Flexible SSL option. Certificates are cheap – e.g. $10 for 3 years, and with the help of your host not that hard to install. Better do it right than get it wrong for your users.
And more importantly – thanks to CloudFlare’s flexible SSL, think twice before providing your personal information on a website even when it shows HTTPS. If you’re extra paranoid, check the certificate and see if it’s signed to ClareFlare’s infrastructure – and if it is, assume the worst – that it’s using the flexible SSL.